Blog
How to manage stakeholders during a cyber-attack
A breach a day is the new norm. In the past 12 months there have been a number of high profile breaches. Take Sony for example, they lost control of their entire network. The hackers were releasing feature length movies onto torrent sites for people to freely download. This was very high profile at the time and it was incredibly damaging. TalkTalk, had all of their customer information dumped onto the internet for everybody to use. XBOX Game Network was hacked over the Christmas period. They had a Distributed Denial of Service – the hackers just wanted to do it for the fun of it! Famous political figures have also had their public profiles very notably defamed.
These hacks happen everyday. A breach a day is the new norm.
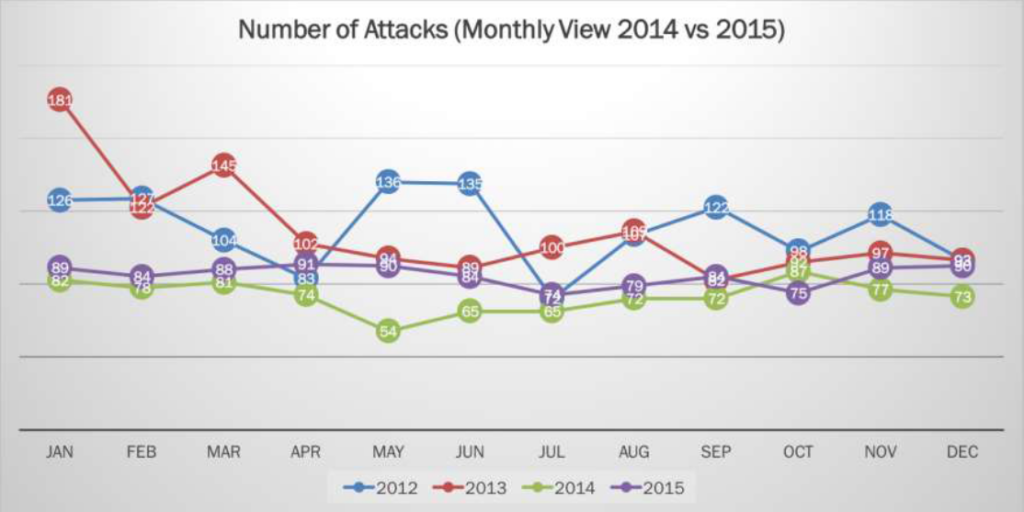
When we look at the trends of monthly attacks from 2012-2015, what we can easily see from this graph is of course those high level more noticeable attacks, but what is also apparent is that there is an on-going trend of attacks that are occurring all of the time. I receive for example, emails regular saying that there has been irregular activity on my various accounts, such as email, or social accounts. And we need to understand how to respond to this.
So how is 2016 shaping up? Well, just today I learned about a hospital having ransom-ware maliciously installed onto their computers, servers and various other devices and receiving a ransom for 1.5M$ – ‘you give us 3000 bit coins or you don’t get your data back – give us your money or we delete your data’. Their data of course has all kinds of patient records, with people expecting results of tests they’ve, had, or details of serious illnesses etc. How can you prepare for when something like this happens?
Here are some questions that you need to think about to help you prepare for a cyber-attack:
What threats could impact your organisation? It is important to understand what type of threat your organisation could experience and the impact it could have. It could be a number of different threats, from loss of services, to a loss of data. Your customers might not be able to continue their online banking or if data is lost, in the case of TalkTalk who lost all of their customer data, the hackers targeted individuals for their bank details.
Do you have a response plan? Hackers generally know that people work from 9am-5pm so often their attacks will occur out of office hours! So you need to have an IT incident response plan in place. What are you going to do if you experience a cyber-attack in the early hours of the morning? Most malicious code is not found for about six months, so how are you going to find out? What method do you have to interact with your organisation to say ‘we think there is something suspicious going on.’ What does your plan say when you find out? What do you do? Who are your stakeholders? These are important questions your IT incident response plan needs to answer.
Who needs to be part in the IT incident response plan?
- IT Security: They are the guys that are most likely going to fix the issue. If you don’t have a security team on hand then you need to define who is going to manage it, in the event that your network has been breached.
- Incident Team: Who is going to co-ordinate the response? Who from your executive team is going to take control of the incident and how are you going to reach them? What is your escalation point into your executive team?
- Legal-counsel: If all of a sudden your customer credit card details are stolen, not only will you need to manage your internal stakeholders, but you will need to include the executive team. You may need legal support.
Who are your stakeholders? There are a number of different stakeholders that you need to think about. If we take a scenario that your customer data has been stolen then you will likely need to work with:
- Marketing – to ensure that you get your messaging right when informing customers about the incident and handling inquiries from the press.
- Customer services – they need to be informed of what has happened and what to expect. You need to ensure that your customer services team can use the right messaging during the incident when talking to customers.
- Employees – your employees need to be informed of a potential ‘red day’ – where they might be lots of calls coming in etc. Your employees need to be forewarned so they know how to take phone calls from customers, from the press and how to escalate queries etc.
- Customers – there is a legal obligation to inform customers of a data breach so you need to think about how you are going to do this and what you are going to say. Having a way to communicate to customers in mass is important.
Here are some simple steps that you should take when preparing the communications in your response plan:
Step 1: Triage – You need to answer the ‘W questions’ – who, what, why, where? And we need to send that information to the stakeholders mentioned above.
Step 2: Inform – How are you going to inform people? Keep in mind that you might be compromised when sending your messages. All messages will get out even if sent securely, so keep the messages open and honest.
Step 3: Manage – Plan how you will keep stakeholders informed – give people an expectation of how and when they are going to be informed.
Step 4: Rehearse – Make sure that that all of the stakeholders know how they are going to be communicated to, which channels they can use and which channels are secure.
To find out more about Everbridge visit: www.everbridge.com


