Top 10 questions to ask when Choosing the right business continuity platform
In today’s environment of heightened risk, operational complexity, and regulatory scrutiny, selecting the right business continuity platform is more than a technical decision—it’s a strategic imperative. Whether you’re a Business Continuity Manager ensuring plan effectiveness, a Risk Officer safeguarding compliance, or an IT Disaster Recovery (DR) leader striving for uninterrupted service delivery, your organization’s resilience depends on having the right tools in place.
Everbridge delivers a business resilience advantage with High Velocity CEM™, protecting organizations from the impact of critical events. By combining market-leading innovation, decision-ready risk intelligence, and full lifecycle automation, Everbridge ensures that managing critical events is as easy as 1-2-3. Only Everbridge helps organizations know earlier, respond faster, and improve continuously.
Selecting the right business continuity platform is a significant decision with long-term implications. It’s therefore essential to ask the right questions to ensure that the chosen solution aligns with your organization’s unique needs. To simplify your due diligence process, we’ve compiled the top 10 questions to ask potential business continuity vendors, along with valuable insights to guide your evaluation.
1. How does the platform centralize data and processes?
A strong platform should consolidate all business continuity, disaster recovery, and risk data into a single system. Centralization ensures consistency by using key data sources, reduces silos, improves visibility, and streamlines decision-making during disruptions.
What to ask:
- What type of templates are provided out of the box to get me started?
- Can the platform integrate data from existing tools like HR, facilities management, IT CMDB, risk management, and incident management solutions?
- Are there standardized import templates to manage my data?
- Does the platform provide an enterprise impact map with a unified view of dependencies and risks in my organization?
- Can I visually see upstream and downstream dependencies to understand single points of failure and critical assets?
- Can the data be segmented between business and IT DR?
- Does the platform provide standard summary reports and dashboards to see the health and status of my program and gaps to be addressed?
2. How configurable and adaptable is the platform?
The platform should be flexible enough to meet your organization’s unique needs while allowing for future growth and changes.
What to ask:
- Can I add new data tables and fields to match my organizational data?
- Are templates, calculations, and reports modifiable?
- How easily can I create new assessment templates, plan templates, and reports?
- Can I enhance a template and retain historical information and responses?
- Do I need technical expertise to apply changes to my templates, calculations, and reports? Does this require engagement with the vendor or a third party?
- Will I still receive upgrades and enhancements if I made configuration changes or modified templates?
3. Does the platform support regulatory compliance?
Compliance is a critical component of business continuity and disaster recovery. The platform should help you meet standards like ISO 22301, FFIEC, FCA, DORA, and SOC 2 while simplifying audit preparation.
What to ask:
- Does the platform provide audit logging of Business Continuity (BC)/DR activities?
- Will I receive updated templates and reports that align with regulatory requirements?
- Is there an automated workflow to alert users when information requires attention or updating?
- Can I easily generate compliance reports to provide to auditors and examiners?

4. What pre-built resources and templates does the platform offer?
Look for platforms that provide ready-to-use templates and workflows aligned with industry standards to save time and ensure consistency.
What to ask:
- Are the templates aligned with industry standards and best practices?
- Do they cover key areas like impact assessments, planning, testing, risk management, and reporting?
- Can templates be easily configured without technical expertise?
- Can I easily modify dropdown options to align with my terminology and resource types?
5. Dependencies
Understanding dependencies is key to effective recovery planning. The platform should visualize upstream and downstream dependencies and identify single points of failure.
What to ask:
- Can I configure the dependency view to see what matters to me?
- Are orphaned records and critical dependencies easily viewable?
- Does the platform provide tools to assess the impact of failures across the organization?
- Can I filter and see key asset dependencies at multiple levels?
- Are dependencies considered when testing my plans?
- Can I see where there are gaps in my response and recovery times for key dependencies such as applications and suppliers?
6. What type of reporting is available in the platform?
All tasks are not the same and should be dynamic based on the response phases and plan type they are associated with.
What to ask:
- Does the platform provide out-of-the-box reports for Business Impact Analysis, Plans, Risks, and Testing?
- Can I create new reports?
- Can reports be automatically sent to stakeholders without manual intervention?
- Are gaps for recovery time objectives (RTOs) easily identified (i.e. application recovery, supply chain, exercises)?
- Are summary reports available to roll data up to location, business entity, or executive leader/stakeholder?
- Can non-licensed users access copies of plans?
- Does the platform provide standard summary reports and dashboards to see the health and status of my program and gaps to be addressed?
7. What automation capabilities does the platform offer?
Automation reduces manual effort and ensures consistency. The platform should support automated workflows for creating, updating, and approving plans, as well as testing and tracking results.
What to ask:
- Can the platform automate alerts, testing, and reporting?
- Does it include automated workflows for cross-departmental collaboration?
- Can workflows be modified based on my organizational settings and frequency for updates?
- Can the platform escalate delinquent activities to leadership for higher levels of visibility and accountability?

8. How does the platform support program visibility?
Dashboards and analytics are essential for tracking program health and readiness. The platform should provide real-time insights and executive-level reporting.
What to ask:
- Can it generate reports that communicate ROI and resilience metrics to stakeholders?
- Does it offer dashboards to visualize program health and readiness?
- Can I create or modify my own reports or do I need to engage with the vendor?
- Can I track the progress of recovery when conducting an exercise/test?
9. Does the planning platform provide integration with critical event management?
Integrating planning with critical event management is essential because it bridges the gap between proactive preparedness and real-time response. Together, they create a seamless, end-to-end approach for managing disruptions, ensuring the plan information is accessible, visible, and leveraged for response activities.
What to ask:
- Does the platform provide automated integration between planning and critical event management for free?
- What information is available from my BIA (Business Impact Analysis) and plan to help make informed decisions regarding impact?
- Can I see the dependencies and resources required for recovery?
- Can I activate plan response strategies and track recovery tasks being completed?
- Does my executive team understand why incidents were invoked and see incident trends over time?
- Does the platform show my team which services to restore and in what order during an incident?
10. What training and support are available?
Even the most intuitive platform requires training and support. The vendor should offer resources to ensure smooth onboarding and long-term success.
What to ask:
- What onboarding and training options are included?
- Is ongoing support available to address future needs and challenges?
- Is support a paid service or included in the subscription?
- Do I need to engage with a third-party vendor for support or changes to myprogram and what is the cost?
- Are there self-service training sessions available if I want to expand my use of theplatform?
- Do I need a license for test participants and infrequent users such as plan or BIAapprovers?
- How long is a typical implementation?
Making a well-informed decision
Choosing the right business continuity platform isn’t just about features; it’s about finding a reliable partner. By asking these 10 questions, you’ll be equipped to identify the best solution for your organization’s needs, ensuring resilience and operational continuity for years to come.

Full transcript
00:05
Hello, my name is Christian Robles and I’m the regional analyst for Latin America in the Caribbean here at Everbridge. We’ve been following this story since mid August when reports first surfaced that the US was deploying naval and air assets into the southern Caribbean.5sAdd a noteJump to
00:22
Early positioning framed as a counter narcotics buildup against so-called narot terrorists in the region. Two months later, that buildup has become a live operation. The US has now conducted 10 confirmed strikes. Eight in the Caribbean Sea and two in the Eastern
00:40
Pacific, killing at least 43 people and capturing two others. The latest strike hit a Drenad Aagua vessel in international waters. And hours later, Washington ordered the deployment of the Gerald R. Ford carrier strike group into the region under US southern command.
01:02
This marks a turning point. What began as targeted interdictions is now a full-scale power projection in the Western Hemisphere. And looking ahead, if this continues, several outcomes are possible. First, the operation could expand beyond the sea. President Trump has said he
01:22
won’t seek a declaration of war and that land operations will be next. That raises the prospect of covert actions inside Venezuela or air strikes on inland targets. Redrawing the map of US engagement in South America. Second, regional alignment is hardening. Colombia accuses Washington of
01:45
extrajudicial killings while Venezuela is mobilizing forces along its borders and warning of asymmetrical warfare. Meanwhile, Trinidad and Tobago is moving the other direction, hosting the destroyer USS Graveley and 2,000 Marines this week for joint exercises. The
02:05
island has become Washington’s southern anchor, a forward partner now facing greater exposure to Venezuelan cyber and intelligence pressures. And third, the commercial impact for shipping energy and insurance. The southern Caribbean is shifting from a patrol zone to a contested operating environment.
02:29
It’s expected temporary port closures in Trinidad and Tobago, higher war risk and detention premiums within 200 nautical miles of Venezuelan waters and strict sanctions screenings as the US expands terror designations. If exclusion zones appear or if Venezuela begins shadowing commercial
02:49
traffic, markets will react quickly. Since August, this campaign has evolved from deterrence to execution. The language deployments and now the carrier group all signal a sustained operational phase. If the tempo continues, the next step could move Finland. A shift that would
03:09
rattle regional stability and the confidence of US companies moving goods, fuel or data through these routes. We’ve been covering this from all angles and the takeaway is clear. We recommend monitoring unfolding events. Each new strike, asset movement signals that this
03:30
operation isn’t slowing, and the longer it runs, the harder it becomes to unwind. I’m Christian Robas, and we’ll continue tracking how these developments shape risk and stability across the region in the days ahead.

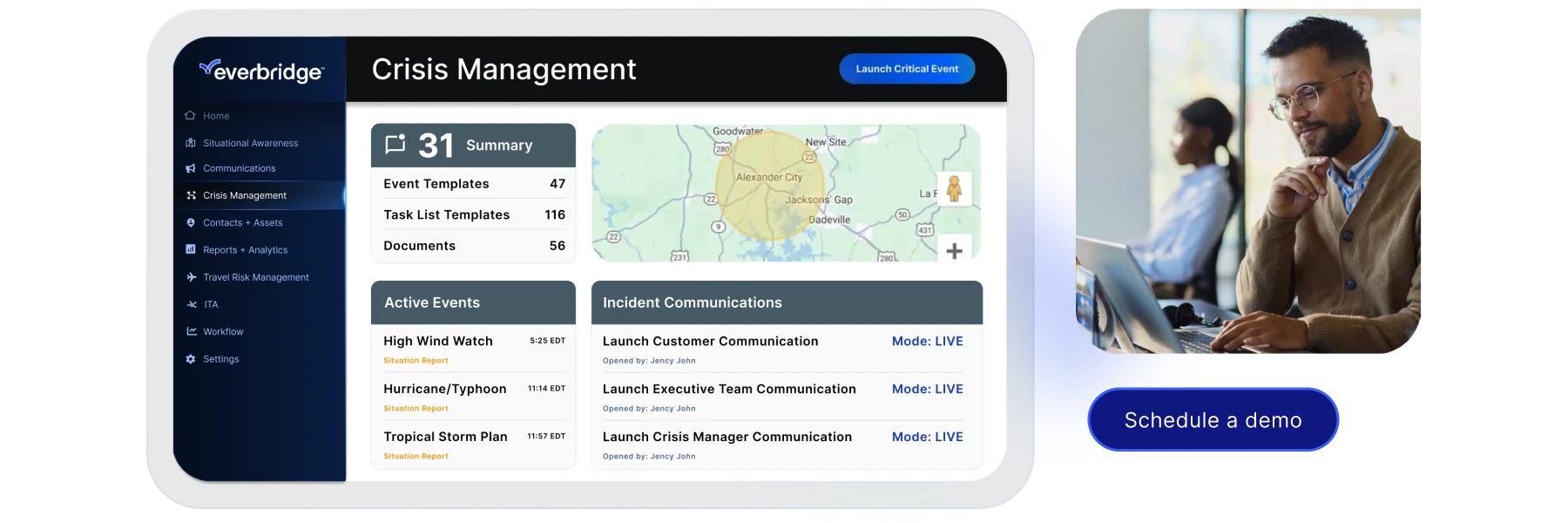
Everbridge 360 integrates advanced communication, real-time risk intelligence, and incident management into one powerful platform. This unified solution streamlines how organizations manage critical events, offering comprehensive oversight. Its two-way mass notification ensures seamless emergency communication with instant updates, real-time feedback, and critical information sharing. This capability is crucial for keeping people safe and operations running smoothly when it matters most. By uniting these powerful tools, organizations can enhance emergency response, minimize communication delays, and ultimately boost both operational efficiency and organizational resilience in the face of any threat.

“Everbridge CEM has transformed how we manage critical events, enabling us to respond faster, ensure our employees’ safety, and maintain seamless operations no matter the challenge.”
– Akamai

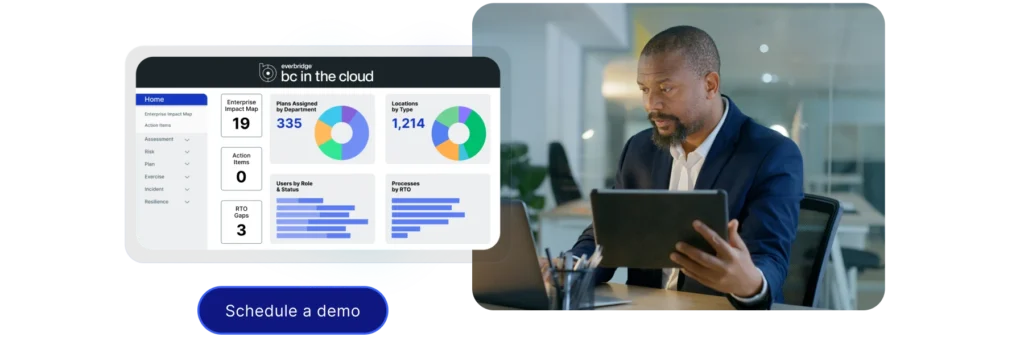
Everbridge BC in the Cloud unites planning, risk management, and response, to strengthen business continuity and disaster recovery while providing flexibility within a low-code platform. With built-in templates and compliance-ready workflows, it streamlines planning, automates processes, maps dependencies, and delivers real-time insights for precise incident response.
Purpose-built for resilience, it empowers organizations to strengthen business continuity and disaster recovery programs, ensuring precise responses across the entire incident lifecycle. From risk assessments to recovery, BC in the Cloud integrates planning, automation, and real-time insights into a streamlined experience.

“BC in the Cloud helps solve the lack of clarity in how organizational processes are defined and their resiliency posture. It helps consolidate and present organizational data through a resiliency lens, driving positive change through data.”
– Thomas B. Senior Business Resilience Manager

Everbridge Travel Protector™ ensures the safety and well-being of employees wherever they travel by providing 360° threat awareness, dynamic travel intelligence, and advanced communication. Travel Protector enables businesses to identify risks, issue pre-trip advisories, and monitor travel plans for VIPs or individuals heading to high-risk destinations. By delivering real-time insights and alerts, it helps organizations proactively address potential dangers, ensuring employees are informed, protected, and supported, no matter where their work takes them. Combined with Everbridge Assist, the Everbridge 24/7 medical & security assistance service, organizations can build comprehensive travel risk management programs that fulfill duty of care requirements, and comply with ISO 31030.

“At Burns & McDonnell, safety is first. With more than 13,500 employees working from 70 offices globally, we are committed to creating safe environments in the office, in the field and while traveling. Everbridge Travel Protector helps keep our teams safe wherever they go.”
– Robert Hope, Director, Burns & McDonnell
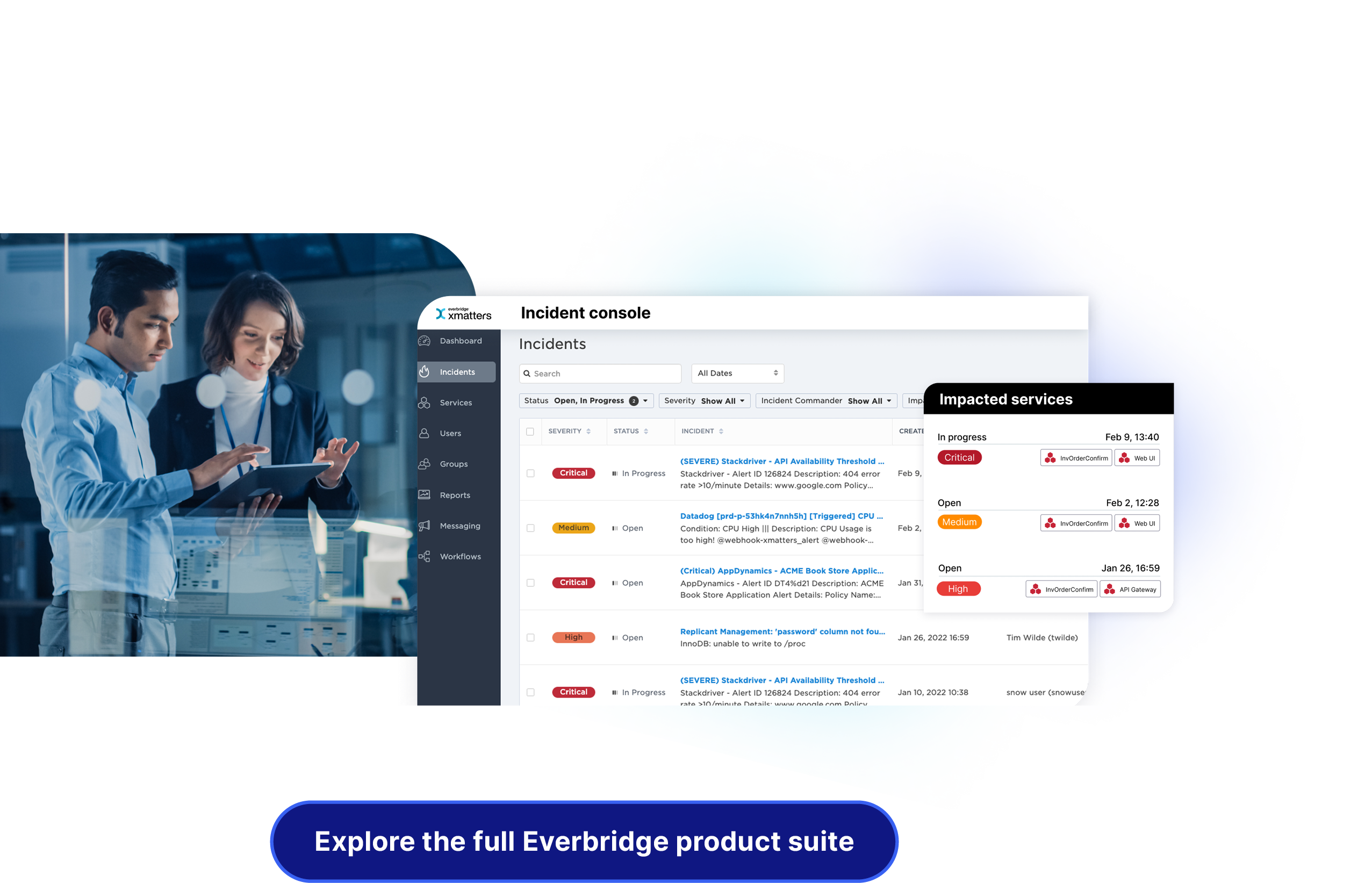
Everbridge xMatters empowers DevOps, SREs, and operations teams with automated workflows to ensure reliable infrastructure and application uptime. By streamlining incident management and enabling efficient collaboration, xMatters reduces risks and helps teams resolve issues quickly. With signal intelligence, adaptive incident management, and actionable analytics, it ensures seamless customer experiences and improved operational performance. xMatters also automates workflows to proactively manage issues associated with new releases, reducing the risk of incidents that could impact customers. Its connected, collaborative workflows provide every team with the tools they need to maintain reliability, minimize downtime, and deliver consistent, high-quality service.

“xMatters is the first step to operating globally. It’s the first thing you need to be able to manage your rotation, manage your paging, and manage your teams and operations.”
– Ben Narramore Director of Global Operations, Sony Interactive Entertainment obert Hope, Director, Burns & McDonnell

Everbridge Control Center integrates safety and physical security systems into a unified platform, providing real-time situational awareness and operational control. It offers automated workflows, enabling the streamlining of processes, accelerating response times, and ensuring consistency in managing incidents. It provides a common operating picture and delivers a cost-advantage by integrating disparate systems like CCTV, access control, and alarm monitoring, into a single-pane-of-glass for global security operations to protect both people and facilities.

Everbridge SnapComms is a multi-channel internal communication platform designed to inform and engage with employees to help achieve 100% message readership. With unique formats like desktop takeover, tickers, and a large library of designer templates, it boosts employee engagement, delivers urgent notifications, and drives action for leadership updates.


The Personal Safety Device (PSD) enhances on-the-go safety for lone workers or those in higher risk work environments. This compact, wearable device offers rapid response, peace of mind, and real-time protection through alerts, location monitoring, and reliable communication when it’s needed most.

Everbridge RedSky provides dynamic, cloud-based E911 solutions to protect mobile workforces and ensure compliance with federal regulations like Kari’s Law and the Ray Baum Act. RedSky solutions ensure that 911 calls get routed to the correct local Public Safety Answering Point (PSAP) during an emergency to protect employees wherever they are.

Signal is an AI-powered intelligence platform that tracks global sources, from social media to the dark web. It delivers real-time insights and early warnings to enhance resilience, protect people, ensure security, and safeguard organizational reputation.

The Everbridge advantage
Everbridge offers the most comprehensive, end-to-end suite of solutions for managing both physical and digital critical events. Powered by Purpose-built AI, our High Velocity CEM™ platform delivers industry-leading actionable risk intelligence to help keep your people safe and organizations running.
The results are clear: Forrester Consulting estimates a 358% ROI for Everbridge customers over three years, including $2 million saved in IT downtime and $3 million gained in operational efficiency. With instant multi-channel notifications and full lifecycle automation, Everbridge streamlines responses, eliminates delays, and strengthens organizational resilience – all within a seamless, user friendly platform.
A unified platform for greater resiliency in critical event management
Leveraging cutting-edge technology, strategic innovation, and proven reliability, Everbridge empowers you to navigate an ever-changing risk landscape with confidence.