Afghanistan–Pakistan escalation raises regional risk
FAA briefly halted El Paso flights over security concerns tied to drone activity and military training, highlighting airspace coordination risks and disruption impacts.

FAA briefly halted El Paso flights over security concerns tied to drone activity and military training, highlighting airspace coordination risks and disruption impacts.
FAA briefly halted El Paso flights over security concerns tied to drone activity and military training, highlighting airspace coordination risks and disruption impacts.
Casey and Shay are joined by Rudy Murillo, Vice President of Emergency Management and Services at the New York City Housing Authority, the largest public housing authority in the United States.
Navigate DORA with confidence. Our 2-part webinar series delivers practical, automated solutions for ICT risk management, incident reporting, and audit readiness.
FAA briefly halted El Paso flights over security concerns tied to drone activity and military training, highlighting airspace coordination risks and disruption impacts.
Bangladesh’s Feb 12, 2026 elections are expected to be managed but may cause short-term, localized disruption. This briefing outlines security, mobility, and operational impacts.
The Milano Cortina 2026 Winter Olympics will heighten risks in Lombardy and northeastern Italy, including petty crime, activism, and disruptions from weather or protests. Spread-out venues and increased crowds could escalate minor issues into major challenges. Proper mitigation strategies will be essential to manage these risks effectively.
Break down silos and boost collaboration. Learn how to improve response times and outcomes. Coordinate physical and cyber incidents in minutes not hours! Can’t miss session.
Join Everbridge at Booth #27091 to learn more about our resilient solutions and strategies to keep your people safe and your business running.
Casey and Shay open with personal quirks before welcoming resilience leader Lisa Jones to unpack cloud risk, SLAs, true redundancy, and leadership lessons that build trust.
Our guide, Safeguarding global mobility, shows how pre-travel and pre-deployment screenings protect your people and business. Ensure you meet your duty of care.
Step into the future of resilience with Everbridge's CEM solutions. Visit us at Booth #1841.
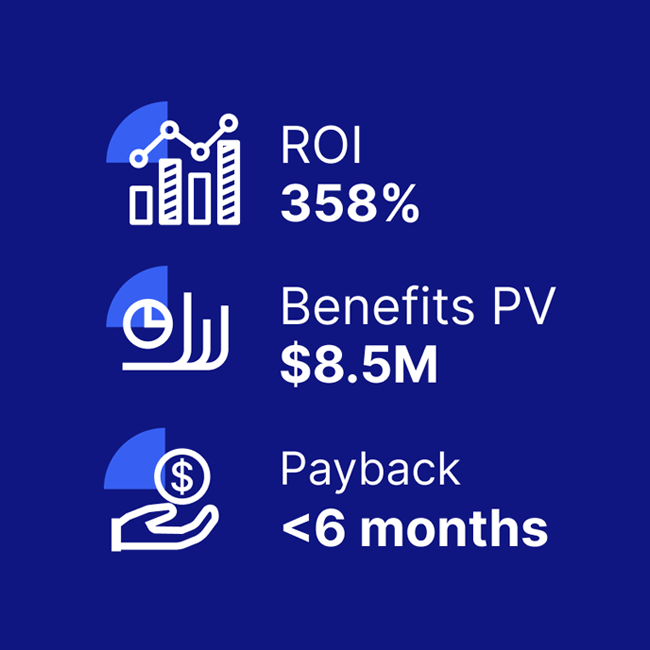
A composite organization comprised of interviewees with experience using the CEM platform achieved a 358% ROI and US$8.5M in three-year risk-adjusted benefits, according to a commissioned Total Economic Impact(TM) Study by Forrester Consulting.
This includes:
Discover the value Everbridge can bring to your organization from our ROI calculator, checklist, and full TEI study.

Everbridge University provides your team with the skills, techniques, concepts, and best practices needed to correctly relay critical communications and manage incidents, allowing you to redeem the full value from your investment.