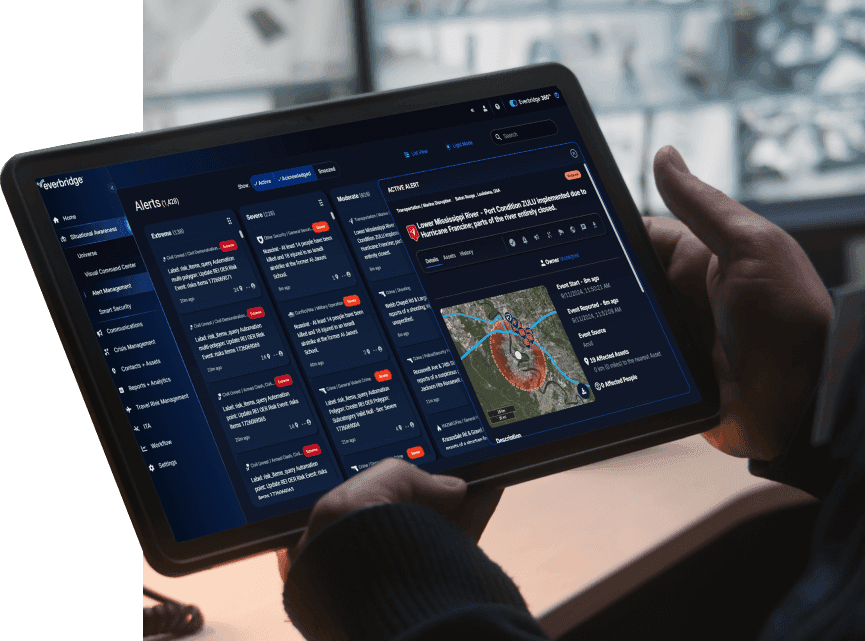
Corporate physical security is the protection of an organization’s personnel, property, data, and physical assets from events that could cause loss or damage. It goes far beyond the traditional image of “guards and gates.”
The modern threat landscape is a complex and evolving environment where physical and cyber risks are increasingly intertwined. Threats now range from sophisticated intrusion attempts and workplace violence to environmental hazards and civil unrest.
How much confidence do you have in your organization’s physical security measures?
A proactive approach to security risk management is essential for business continuity and workplace safety. Organizations require a clear, comprehensive strategy to address these challenges effectively.
Understanding today’s physical security threats
To build a resilient security posture, you must first understand the full spectrum of threats. Here are 10 common physical security threats to be aware of:
External threats
These threats come from outside the organization and can have severe consequences.
1. Unauthorized access & intrusion
Methods like tailgating, social engineering, and forced entry remain common tactics for gaining illicit access to facilities.
2. Theft
This includes not only the theft of physical assets like equipment and inventory but also the theft of invaluable intellectual property.
3. Vandalism & sabotage
Malicious actors can cause significant property damage, disrupt operations, and incur substantial repair costs.
4. Physical violence
The potential for threats from external actors, including disgruntled former employees or targeted attacks, requires dedicated active assailant incident planning.
5. Civil unrest
Protests and social instability can spill over, leading to business disruptions, looting, vandalism, or violence near corporate premises.
6. Natural disasters
Fires, floods, and extreme weather events can cause catastrophic damage to facilities, leading to prolonged downtime. For example, the 2021 Texas power crisis caused by a severe winter storm resulted in widespread outages, impacting countless businesses.
7. Environmental hazards
Chemical spills, poor air quality from events like wildfires, and other environmental incidents can threaten employee health and disrupt operations.
Internal threats
Threats from within the organization can be just as damaging as external ones, often exploiting trusted access.
8. Employee theft or fraud
Malicious insiders with legitimate access can steal assets or commit fraud, causing significant financial and reputational harm.
9. Unintentional breaches
Employees can unintentionally compromise security by leaving doors unsecured, losing access cards, or falling prey to social engineering scams.
10. Workplace violence
Situations involving disputes between employees, early intervention, and effective workplace policies are critical in mitigating these risks.
Developing a robust physical security strategy
A successful corporate physical security plan is built on a layered defense model. The “Deter, Detect, Delay, Mitigate, and Respond” framework provides a foundational structure for creating a comprehensive and effective security strategy.
- Deter:
Implement measures to discourage potential threats, such as visible security personnel, exterior lighting, and clear signage. - Detect:
Use surveillance systems, alarms, and access control to identify threats as early as possible. - Delay:
Incorporate barriers, reinforced doors, or security checkpoints to slow down or prevent unauthorized access. - Mitigate:
Develop and deploy contingency plans, safety training, and redundant systems to minimize the impact of incidents. - Respond:
Establish protocols for rapid response, including communication strategies, evacuation plans, and crisis management teams.
Alongside this framework, your security plan must include:
- Access controls:
This is the foundation of physical security. It involves physical barriers like fences and gates, complemented by electronic systems such as keycard readers, biometric scanners, and mobile credentials to manage entry. - Surveillance and monitoring:
Strategically placed video cameras (IP, PTZ, panoramic) provide real-time monitoring and forensic evidence. These are supported by alarm systems and sensors that detect intrusion, glass breaks, and motion. Utilize AI-powered surveillance systems that use advanced video analytics to automatically detect threats, recognize suspicious behaviors, and alert security personnel in real-time. - Perimeter security:
Securing the outer boundaries of a property with effective lighting, physical barriers, vehicle access gates, and regular security guard patrols is the first line of defense against external threats.
8 Steps to create a corporate physical security strategy
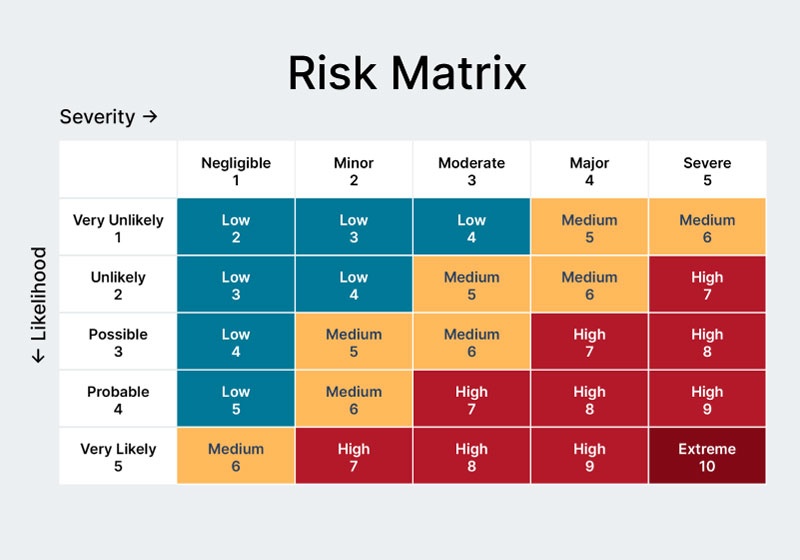
1. Conduct a security risk assessment
The first step in developing a physical security plan is to perform a thorough risk assessment. This process identifies potential threats, vulnerabilities, and critical assets that need protection. These are then prioritized in a risk matrix assessed by likelihood to occur and potential impact.
You should evaluate numerous factors, such as crime rates in the area, internal risks like employee misconduct, and environmental concerns such as natural disasters. Then, based on your risk analysis, prioritize and implement risk mitigation measures that provide the greatest risk reduction.
2. Define security objectives
Clearly outline the goals of the security plan based on the results of the risk assessment. Objectives may include safeguarding employees, preventing unauthorized access, ensuring compliance with regulatory requirements, minimizing loss during security incidents, or building operational resilience. Defining these objectives helps align security initiatives with organizational priorities.
3. Inventory existing security measures
Take stock of any existing security infrastructure and protocols, such as access controls, surveillance systems, emergency response plans, and systems. Assess the performance of these measures to identify gaps or areas needing upgrades. This evaluation ensures that resources are utilized effectively and helps avoid redundancy.
4. Develop layered security measures
Adopt a multi-layered approach to physical security by combining various strategies such as policy implementation, access control systems, intrusion detection technology, critical event management systems, and robust perimeter defenses.
Integrating these measures creates multiple barriers that deter or delay potential threats. The layered approach ensures both proactive and reactive protection.
5. Design emergency response protocols
Establish clear and actionable response plans for various scenarios, including fires, active assailants, intrusions, and natural disasters.
These protocols should be designed to prioritize safety, minimize confusion, and facilitate a swift resolution. Include communication plans to notify key stakeholders and coordinate with law enforcement or emergency responders if necessary.
6. Integrate technology and automation
Leverage advanced technologies to enhance security operations. This may include automated access management systems, AI-powered surveillance for real-time threat detection, or centralized monitoring platforms.
7. Train employees and conduct drills
Employees are a critical component of any security strategy. Technology alone is insufficient, as it can be undermined by human error. Comprehensive employee training programs are essential to foster a security-conscious culture.
Hold regular training sessions to educate employees on recognizing and reporting suspicious activities, understanding emergency procedures, and adhering to access control protocols. Conducting periodic emergency drills or tabletop exercises ensures readiness and identifies areas for improvement.
8. Monitor and evaluate performance
Security plans should be dynamic, not static. Regularly monitor the effectiveness of the implemented measures through audits, inspections, and performance metrics.
Use data from incidents or simulations to refine the plan as needed. Schedule periodic risk assessments and penetration tests to identify new vulnerabilities. Your plan should be updated based on these findings, as well as changes in the threat landscape, business operations, or technology.
Securing your organization’s future
A modern corporate physical security strategy requires a proactive, multi-layered approach that integrates technology, processes, and people. The future of security lies in the convergence of physical and cybersecurity, driven by predictive analytics and unified platforms.
By adopting a comprehensive security risk management framework, you can build a resilient organization prepared to face today’s threats and enhance workplace safety and security.
Ready to unify your security operations and gain a complete picture of your risk landscape? Get a demo of Everbridge to see how our platform can transform your security strategy.