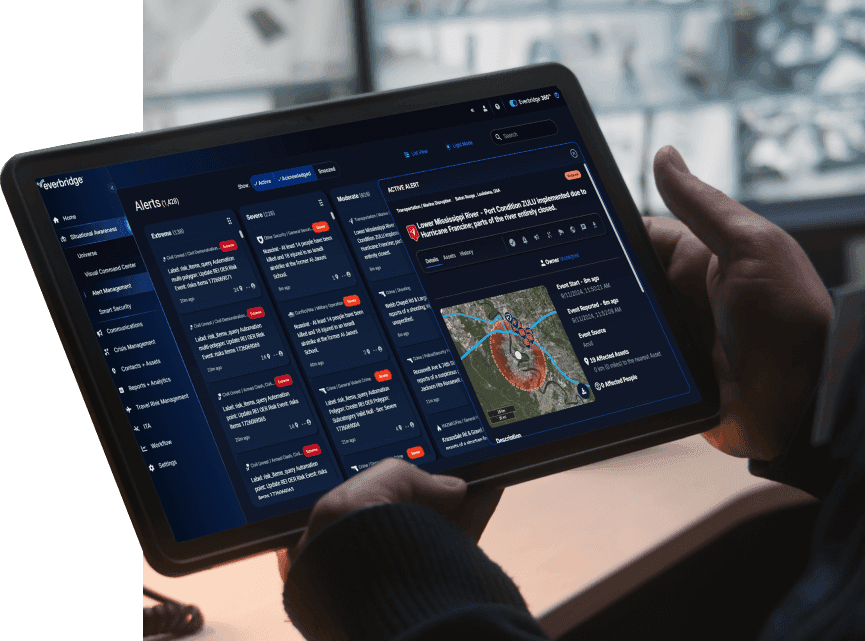
Managing security & risk 2.0

Related resources

Independent Bank’s secret to resilient BCP: Everbridge
Discover how Independent Bank leverages Everbridge to streamline communication, enhance response times, and ensure compliance during critical events. From managing BCP notifications to navigating unexpected challenges, see why Everbridge is their go-to solution for resilience and efficiency.

Burns & McDonnell enhances global safety and resilience with Everbridge
Burns & McDonnell leverages Everbridge to enhance global safety and resilience by managing weather emergencies, ensuring traveler safety, and protecting their workforce and operations.