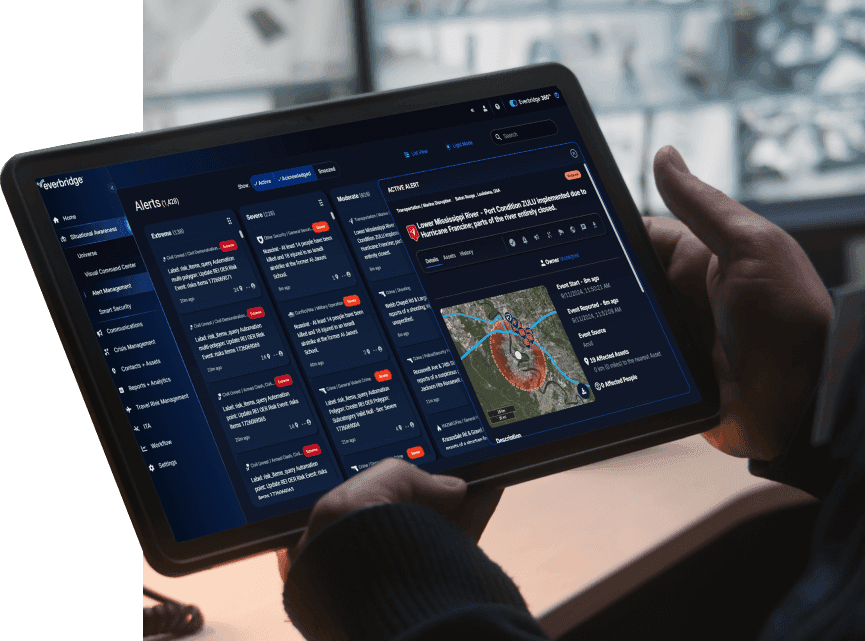
Corporate physical security is the protection of an organization’s personnel, property, data, and physical assets from events that could cause loss or damage. It goes far beyond the traditional image of “guards and gates.”
The modern threat landscape is a complex and evolving environment where physical and cyber risks are increasingly intertwined. Threats now range from sophisticated intrusion attempts and workplace violence to environmental hazards and civil unrest.
How much confidence do you have in your organization’s physical security measures?
A proactive approach to security risk management is essential for business continuity and workplace safety. Organizations require a clear, comprehensive strategy to address these challenges effectively.
Understanding today’s physical security threats
To build a resilient security posture, you must first understand the full spectrum of threats. Here are 10 common physical security threats to be aware of:
External threats
These threats come from outside the organization and can have severe consequences.
1. Unauthorized access & intrusion
Methods like tailgating, social engineering, and forced entry remain common tactics for gaining illicit access to facilities.
2. Theft
This includes not only the theft of physical assets like equipment and inventory but also the theft of invaluable intellectual property.
3. Vandalism & sabotage
Malicious actors can cause significant property damage, disrupt operations, and incur substantial repair costs.
4. Physical violence
The potential for threats from external actors, including disgruntled former employees or targeted attacks, requires dedicated active assailant incident planning.
5. Civil unrest
Protests and social instability can spill over, leading to business disruptions, looting, vandalism, or violence near corporate premises.
6. Natural disasters
Fires, floods, and extreme weather events can cause catastrophic damage to facilities, leading to prolonged downtime. For example, the 2021 Texas power crisis caused by a severe winter storm resulted in widespread outages, impacting countless businesses.
7. Environmental hazards
Chemical spills, poor air quality from events like wildfires, and other environmental incidents can threaten employee health and disrupt operations.
Internal threats
Threats from within the organization can be just as damaging as external ones, often exploiting trusted access.
8. Employee theft or fraud
Malicious insiders with legitimate access can steal assets or commit fraud, causing significant financial and reputational harm.
9. Unintentional breaches
Employees can unintentionally compromise security by leaving doors unsecured, losing access cards, or falling prey to social engineering scams.
10. Workplace violence
Situations involving disputes between employees, early intervention, and effective workplace policies are critical in mitigating these risks.
Developing a robust physical security strategy
A successful corporate physical security plan is built on a layered defense model. The “Deter, Detect, Delay, Mitigate, and Respond” framework provides a foundational structure for creating a comprehensive and effective security strategy.
- Deter:
Implement measures to discourage potential threats, such as visible security personnel, exterior lighting, and clear signage. - Detect:
Use surveillance systems, alarms, and access control to identify threats as early as possible. - Delay:
Incorporate barriers, reinforced doors, or security checkpoints to slow down or prevent unauthorized access. - Mitigate:
Develop and deploy contingency plans, safety training, and redundant systems to minimize the impact of incidents. - Respond:
Establish protocols for rapid response, including communication strategies, evacuation plans, and crisis management teams.
Alongside this framework, your security plan must include:
- Access controls:
This is the foundation of physical security. It involves physical barriers like fences and gates, complemented by electronic systems such as keycard readers, biometric scanners, and mobile credentials to manage entry. - Surveillance and monitoring:
Strategically placed video cameras (IP, PTZ, panoramic) provide real-time monitoring and forensic evidence. These are supported by alarm systems and sensors that detect intrusion, glass breaks, and motion. Utilize AI-powered surveillance systems that use advanced video analytics to automatically detect threats, recognize suspicious behaviors, and alert security personnel in real-time. - Perimeter security:
Securing the outer boundaries of a property with effective lighting, physical barriers, vehicle access gates, and regular security guard patrols is the first line of defense against external threats.
8 Steps to create a corporate physical security strategy
1. Conduct a security risk assessment
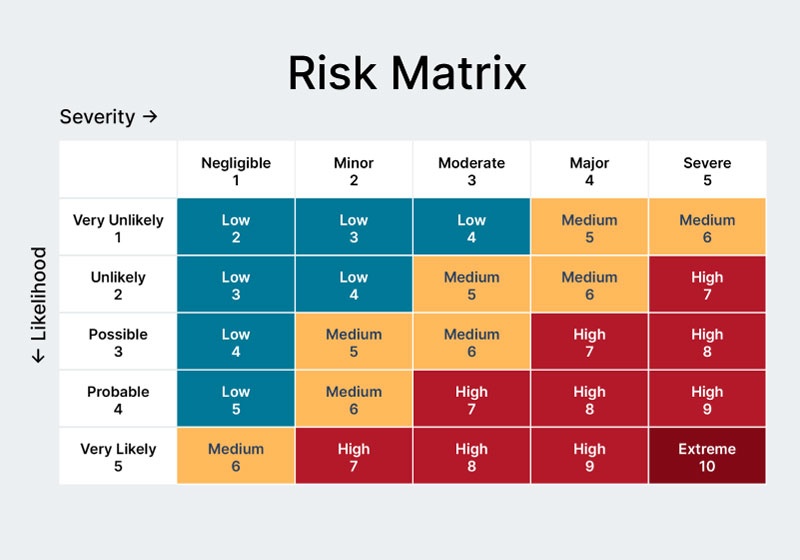
The first step in developing a physical security plan is to perform a thorough risk assessment. This process identifies potential threats, vulnerabilities, and critical assets that need protection. These are then prioritized in a risk matrix assessed by likelihood to occur and potential impact.
You should evaluate numerous factors, such as crime rates in the area, internal risks like employee misconduct, and environmental concerns such as natural disasters. Then, based on your risk analysis, prioritize and implement risk mitigation measures that provide the greatest risk reduction.
2. Define security objectives
Clearly outline the goals of the security plan based on the results of the risk assessment. Objectives may include safeguarding employees, preventing unauthorized access, ensuring compliance with regulatory requirements, minimizing loss during security incidents, or building operational resilience. Defining these objectives helps align security initiatives with organizational priorities.
3. Inventory existing security measures
Take stock of any existing security infrastructure and protocols, such as access controls, surveillance systems, emergency response plans, and systems. Assess the performance of these measures to identify gaps or areas needing upgrades. This evaluation ensures that resources are utilized effectively and helps avoid redundancy.
4. Develop layered security measures
Adopt a multi-layered approach to physical security by combining various strategies such as policy implementation, access control systems, intrusion detection technology, critical event management systems, and robust perimeter defenses.
Integrating these measures creates multiple barriers that deter or delay potential threats. The layered approach ensures both proactive and reactive protection.
5. Design emergency response protocols
Establish clear and actionable response plans for various scenarios, including fires, active assailants, intrusions, and natural disasters.
These protocols should be designed to prioritize safety, minimize confusion, and facilitate a swift resolution. Include communication plans to notify key stakeholders and coordinate with law enforcement or emergency responders if necessary.
6. Integrate technology and automation
Leverage advanced technologies to enhance security operations. This may include automated access management systems, AI-powered surveillance for real-time threat detection, or centralized monitoring platforms.
7. Train employees and conduct drills
Employees are a critical component of any security strategy. Technology alone is insufficient, as it can be undermined by human error. Comprehensive employee training programs are essential to foster a security-conscious culture.
Hold regular training sessions to educate employees on recognizing and reporting suspicious activities, understanding emergency procedures, and adhering to access control protocols. Conducting periodic emergency drills or tabletop exercises ensures readiness and identifies areas for improvement.
8. Monitor and evaluate performance
Security plans should be dynamic, not static. Regularly monitor the effectiveness of the implemented measures through audits, inspections, and performance metrics.
Use data from incidents or simulations to refine the plan as needed. Schedule periodic risk assessments and penetration tests to identify new vulnerabilities. Your plan should be updated based on these findings, as well as changes in the threat landscape, business operations, or technology.
Securing your organization’s future
A modern corporate physical security strategy requires a proactive, multi-layered approach that integrates technology, processes, and people. The future of security lies in the convergence of physical and cybersecurity, driven by predictive analytics and unified platforms.
By adopting a comprehensive security risk management framework, you can build a resilient organization prepared to face today’s threats and enhance workplace safety and security.
Ready to unify your security operations and gain a complete picture of your risk landscape? Get a demo of Everbridge to see how our platform can transform your security strategy.
Today’s leaders are more exposed than ever before, due to constant digital connectivity and public visibility. This new era brings complex risks that go far beyond traditional physical security. Successful executive protection now requires a strategy that addresses both digital and physical threats, often occurring at the same time.
Recent high-profile incidents highlight the rising challenges. Organizations have a duty of care to protect their leaders, but is your executive protection program keeping pace with increasing risks? A new study undertaken by ASIS International and Everbridge uncovers critical gaps and opportunities, and this post explores how the threat landscape is evolving, what challenges organizations face, and the key strategies to build a robust protection program.
Executive protection in a shifting threat environment
Executive protection has surged up the agenda. According to the new study, 42% of security professionals report a significant increase in focus on executive protection in just the past 18 months, a clear response to a rapidly growing and evolving threat landscape.
Two major drivers are fueling this urgency:
- Rising public threats (72%): Social media and online forums amplify dissent and anger, often breeding direct threats against executives.
- High-profile incidents (69%): Events such as the assassination of a prominent CEO in 2024 have put executive risk on center stage for boards and security leaders.
The lesson is clear: executive visibility, including digital presence and company communications, increases vulnerability. Threats are now global, persistent, and often initiated online.
The modern threat: where digital meets physical
Threats today arise from the intersection of online and offline worlds, creating complex scenarios that traditional security alone cannot address.
Physical threats enhanced by technology
Traditional kidnapping and assault scenarios have evolved. Attackers use digital tools to plan incidents, analyze public routines, and bypass conventional security. Publicly shared information makes executives’ movements predictable, while personal tech can compromise safety almost anywhere.
Escalating cybersecurity threats
Cyberattacks against executives are more frequent and sophisticated. Deepfake technology, for example, can create fake video calls and social media content nearly indistinguishable from reality. One organization lost $25.6 million in 2024 when a finance employee joined a deepfake video call with “colleagues.” Online intimidation and digital surveillance are now common precursors to real-world attacks.
Challenges holding back executive protection
As risks mount, many organizations struggle to implement effective protection programs. The recent ASIS and Everbridge research spotlights disconnections between awareness, funding, and action.
Budget and executive buy-in
Budget limitations (58%) are the largest barrier, followed by executive non-compliance (47%). These challenges reinforce one another: without executive support, security programs lack funding; without resources, their value remains unproven. For programs to succeed, security must be framed as a business enabler, key to continuity, reputation, and leadership confidence, not as a mere checkbox.
Gaps between awareness and action
According to the ASIS and Everbridge research, there are stark differences between how important security professionals rate various practices and their ability to implement them:
- Online threat monitoring: 65% say it’s critical; only 51% feel equipped to do it well.
- Protecting digital assets & secure communications: 57% rate it highly; just 42% feel capable.
- Behavioral threat profiling: 48% see it as important; only 33% have solid capabilities.
These gaps reveal that while digital risks are widely recognized, many organizations aren’t yet equipped to manage them effectively.
Key strategies for modern executive protection
To address these challenges, organizations must modernize their approaches, merging analysis, technology, and people.
Integration of digital and physical security
Threats originating online can escalate rapidly into the physical world. Effective executive protection uses open-source intelligence (OSINT) and social media monitoring not just to track sentiment, but to identify specific, actionable threats. The study found that while OSINT is widely used (82%), most organizations lack the tools for real-time analysis or behavioral threat detection. Investing in these technologies makes it possible to move from reactive to proactive risk management.
Proactive travel risk management
Executive travel is still a top exposure. Yet many companies take a piecemeal approach:
- 18% rarely or never assess travel risks in advance.
- 25% don’t offer pre-travel safety briefings.
- 30% only monitor intelligence after a known threat arises.
This reactive stance leaves executives vulnerable. Best practices demand pre-trip risk assessments for every journey, thorough briefings, and ongoing monitoring, not just after a threat emerges.
Governance and training
High-level support is essential. Board oversight, adequate resources, and executive participation in security planning are crucial, not just for physical threats but as part of broader cybersecurity compliance. New SEC rules underline the need for C-suite involvement.
Yet training often lags. While situational awareness training is common, scenario-based exercises are rare, despite being invaluable for testing protocols. Fewer than half of organizations offer executives training in emergency procedures, IT security, or even self-defense, leaving many leaders unprepared for new-age threats.
Building a culture of security
Technology is only half the battle. Fostering a culture where leaders understand risks, model best practices, and cooperate with security staff is vital. Security teams should track incidents and measure the effectiveness of their programs, using data to make the business case for ongoing investment.
The path forward: resilient, data-driven protection
To secure buy-in and resources, security leaders must present protection as a strategic investment and support this with measurable results. Yet, according to the ASIS and Everbridge study, more than a third of organizations lack any formal evaluation process for executive protection.
By implementing clear KPIs, tracking incidents, and analyzing outcomes, organizations can demonstrate value, adjust tactics, and ensure constant improvement.
As the threat landscape grows more complex, protecting today’s high-profile leaders demands an integrated, data-driven approach. Digital and physical security must operate in tandem, powered by proactive intelligence, solid processes, board support, and comprehensive training.
Is your protection program evolving with the times? To benchmark your organization or learn how to strengthen executive protection, download the full Executive Threat Environment Report.
Want deeper insights and practical advice? Watch our on-demand webinar, Executive Protection in a Volatile World, and gain strategies directly from leading experts.
Discover how Ameren leverages Everbridge to stay resilient during Midwest weather disruptions and ensure regulatory compliance for nuclear facilities. From location-based notifications with maps to customizable forms for external stakeholders, Everbridge transforms how Ameren handles critical events.
Full video transcript
[00:11.4]
Everbridge has changed the way my team responds to disruptions and critical events in a variety of ways. One way I can think of is, we tend to have bad weather in the Midwest. Inclement weather, whether it’s like, tornado season, whether it’s fire season, or even in the winter.
[00:31.5]
It always kind of poses, challenges operationally and also just for coworkers trying to get to their work center.
[00:44.9]
One thing that happened this winter was that there was a massive, snow and ice storm and business segments were scrambling, trying to figure out who was going to be able to be remote, who was going to be able to work where. And Everbridge really came in key there because there’s a really nice function, with their incidents and notifications that allows you to kind of create an ad hoc HTML, little web page.
[01:08.8]
And that page you can actually add valuable, visual information like maps. So we were able to utilize this function and send texts to key, employees at specific locations, because Everbridge also allows you to put in specific location information for employees.
[01:27.2]
So we were able to target the employees who work at specific places and then send them key information just pertinent to them so they knew, where was safe to drive and where wasn’t, and it also kind of helps other employees know, okay, if we sent you a certain message, you don’t report to work.
[01:44.9]
But if we sent you this message with maps and information, then you know exactly how to get to work and exactly where to park and where the safe spots are.
[01:57.5]
The one way Everbridge has helped my organization stay resilient is just how customizable it is to situations that might happen to differt business segments. One such time is we support, nuclear facilities, and one of the nuclear facilities needed to find a way to send customizable information to external stakeholders that needed to be received in a very specific amount of time and acknowledged in order to maintain, regulatory compliance with their governing body.
[02:32.3]
So through Everbridge we were able to engage some professional services and build out really, really complex forms that had various ways to input information. So they were like dropdown toggles. There was a place for manual input, and it was great because it allowed them to achieve the level of granularity that was necessary.
[02:53.8]
And then send that to external stakeholders who were simply able, type like yes, or whatever they needed, to respond within the allotted time. This was vastly different than the system that they were using before, in the best possible way. We could see that data visualized exactly when people responded, who responded.
[03:13.1]
And we had the flexibility to send it to, specific people within an organization. So it was just incredible. The nuclear team is using it and they’re loving it. And we are constantly in conversations about how we can further expand.