IT incidents can bring businesses to a standstill, impacting productivity, revenue, and reputation. To navigate these challenges, organizations must implement robust IT incident management strategies. This blog offers a comprehensive guide on best practices, communication readiness, and the critical role of technology in incident management.
Understanding the impact of IT incidents
Every day, operational issues such as IT outages and data breaches disrupt business operations. These incidents not only lead to production slowdowns and delayed responses to time-sensitive issues but also require diligent tracking to comply with industry regulations. The true cost of these incidents extends beyond immediate financial losses, affecting customer trust and employee productivity. A well-structured incident management plan is essential to mitigate these impacts effectively.
IT incident management best practices
- Efficient workflows and integration: inefficient workflows across disparate systems slow down incident response. Integrating monitoring and ITSM platforms with communication solutions ensures seamless information flow, enabling faster response times and reducing Mean Time to Repair (MTTR).
- Proactive communication: limiting communication to email and SMS can result in missed alerts. Utilizing a robust communication platform that supports various channels and integrates with on-call schedules helps ensure timely and accurate information reaches the right teams and stakeholders.
- Comprehensive incident management plan: a total incident management plan encompasses preparation, assessment, response, and delivery. Organizations must have clear procedures for communicating with clients, employees, and stakeholders before, during, and after an incident.
- Regular assessment and preparedness: regularly assess communication plans and incident procedures to ensure readiness. This includes having contact methods in place to reach key stakeholders quickly and establishing mechanisms to evaluate the effectiveness of communication processes post-incident.
The role of technology in enhancing incident management
Technology plays a pivotal role in streamlining incident management. Everbridge’s solutions automate communication and ensure consistent, error-free messaging across incidents. By leveraging technology, organizations can enhance situational awareness, facilitate faster collaboration, and ultimately achieve quicker resolution of incidents.
Future-proof your organization
IT vulnerabilities are ever-increasing and mastering IT incident management is not just advantageous but necessary. By implementing the best practices outlined above and harnessing the power of technology, organizations can better prepare for, manage, and recover from IT incidents. To explore how Everbridge can support your organization’s incident management efforts schedule a demo or watch our webinar on cybersecurity preparedness and protection.
Cyber breaches are a constantly evolving combination of threats and security concerns that can put organizations in turmoil. They require not only technical expertise but also strategic stakeholder management. From high-profile breaches like Sony’s network compromise to the ransomware attack on a hospital demanding $1.5 million, organizations face an ever-increasing threat landscape. Understanding how to manage stakeholders during a cyber-attack and adopting evolving strategies for breach detection are crucial for maintaining resilience.
The critical role of stakeholder management in cyber-attacks
Effective management during a cyber-attack starts with a well-defined response plan. Recognizing potential threats and understanding their impact is foundational. From service disruptions to data breaches, such as TalkTalk’s customer data leak, the repercussions can be severe. It’s essential to have a plan that operates 24/7, as attacks often occur outside regular business hours. Key components include:
- IT security and incident teams: these are the frontline defenders. Ensure you have a dedicated team ready to address breaches and coordinate responses.
- Legal counsel: engage legal advisors to manage compliance and potential liabilities if sensitive data is compromised.
- Stakeholders: identify and communicate with all relevant parties, such as marketing, customer service, and employees, to ensure consistent messaging and support during an incident.
Developing a communications plan is also critical. Steps include triaging information to stakeholders, informing them through secure channels, managing ongoing updates, and regularly rehearsing these processes to ensure preparedness.
Shifting strategies: from prevention to detection
The landscape of cybersecurity risk management is evolving. While prevention remains a priority, the focus has increasingly shifted towards detection. This shift acknowledges the sophistication of modern threats and the inevitability of breaches. Key strategies include:
- Automation: leveraging automated tools for monitoring and incident management can significantly enhance detection capabilities. Automation helps in quickly identifying threats and reduces the impact on operations.
- Threat intelligence: organizations should utilize advanced threat intelligence to anticipate risks and integrate this data into automated systems for improved resilience.
- Industry collaboration: joining industry groups and staying informed about local and global cybercrime trends can help organizations stay ahead of potential threats.
Preparing for the future
Embracing these strategies ensures organizations are better equipped to handle cyber threats. Begin by evaluating the automation tools necessary for your organization’s needs and considering the return on investment for implementing these technologies.
For over two decades, Everbridge has been at the forefront of critical event management, helping businesses enhance their cybersecurity defenses. To understand more about achieving cyber resilience, watch our latest webinar on strengthening your cyber defenses:
Cybersecurity in financial services presents unique challenges in strengthening resilience against potential threats. Financial institutions not only need to combat cyber threats such as web application attacks, bad bots, ransomware, and phishing attacks, but also maintain uptime before, during, and after such breaches to ensure seamless customer service and regulatory compliance.
The cost of cybersecurity risks
According to IBM’s Cost of a Data Breach Report 2024, the global average cost of a data breach reached USD 4.88 million, a 10% increase from the previous year and the highest total ever recorded. A third of breaches involved shadow data, highlighting the difficulties in tracking and safeguarding proliferating data. Organizations using security AI and automation extensively in prevention reported average cost savings of USD 2.22 million compared to those that didn’t. Beyond these staggering statistics, financial institutions face even greater fears in lost business costs, including increased customer turnover, lost revenue due to downtime, and the rising cost of acquiring new business due to diminished reputation.
Regulatory landscape
The FFIEC (Federal Financial Institutions Examination Council) has strengthened its mandates for operational resilience, business continuity, and crisis management within the financial sector. This increase in regulation and compliance expectations underscores the necessity of automation across operational risk areas to achieve efficiency in processes, knowledge, and impact assessment. Regulators focus on the impacts of operational outages and their industry-wide effects, requiring detailed tracking, audit logs, and evidence of executive oversight.
The importance of cyber resilience
For financial services to succeed amidst heightened regulatory requirements and complex digital threats, cyber resilience extends beyond simply remediating attacks. It involves maintaining a reputable and trustworthy brand and product for customers. Organizations must prioritize building a resilient operation so that any disruption, whether from a cyberattack or other causes, has minimal impact on customer experience and avoids major non-compliance fines. Through digital transformation and a commitment to automation, financial institutions can build maximum operational resilience, enhance customer experience, and achieve positive returns on technology investment.
The domino effect of disruptions
Digital disruptions in large financial firms can have cascading negative impacts. Cybersecurity-related risks can lead to direct costs for affected banks and ripple effects on counterparties within the financial sector and the broader economy. Becoming cyber resilient means more than shielding against a single disruption; it requires active prevention against the negative domino effect such disruptions can trigger. With much of the financial sector’s success rooted in customer trust, falling victim to a chain of events that impact on the economy puts institutions at high risk of lost business. It truly pays to be prepared.
Operational resilience through digital transformation
Innovations in incident management, including greater automation, integration, data-level visibility, and user-friendly advances, support the infrastructure necessary for uninterrupted customer experiences. Everbridge critical event management can help financial services establish and maintain ‘Operational Resiliency ROI’ by minimizing business downtime and accelerating incident resolution through automated communications, collaboration, and orchestration. It streamlines incident response across IT Ops, Service Ops, Sec Ops, DevOps, and IT BC/DR, equipping employees with the information and resources needed to support digital transformation and deliver uninterrupted customer experiences.
For more insights, watch our webinar on cybersecurity preparedness and protection.
Cyber threats are becoming increasingly sophisticated and frequent, posing significant risks to business operations, financial stability, and reputational integrity. For modern organizations, cybersecurity preparedness is not just a strategic advantage, but a critical necessity. Everbridge, a leader in critical event management, offers a comprehensive approach to cyberattack prevention that transforms how businesses respond to and recover from cyber incidents.
Understanding cybersecurity preparedness
Cybersecurity preparedness refers to the proactive planning and implementation of measures to prevent, detect, respond to, and recover from cyber incidents. It encompasses various activities such as risk assessment, vulnerability management, incident response planning, continuous monitoring, and fostering a culture of cybersecurity awareness. In essence, it is about building resilience against cyber threats to ensure operational continuity and protect sensitive information.
The importance of cybersecurity preparedness
To downplay the importance of cybersecurity planning would mean to commit a fatal mistake. The ENISA Threat Landscape 2023 report highlights ransomware and DDoS attacks as predominant threats, with public administration being the most targeted sector, enduring nearly 19% of attacks. LockBit ransomware accounts for almost half of ransomware incidents, while phishing leads to a 10% rise in Business Email Compromise complaints, resulting in losses over $2.7 billion.
DDoS attacks are widespread, affecting 13% of Cloudflare customers in 2022, and DNS request flooding increased by 93.4%. TCP-based attacks make up 63% of attack traffic. Alarmingly, 82% of data breaches involve human factors, stressing the need for enhanced security awareness. The IBM 2024 report notes that the average cost of a data breach reached $4.88 million, the highest total ever, urging businesses to invest in cybersecurity frameworks and employee training.
Real-world incidents happening all over the world underscore the severe implications of cyber threats, affecting numerous government agencies and businesses as reported by the Center for Strategic & International Studies. By investing in cybersecurity, organizations can mitigate risks and protect their assets. Implementing comprehensive security protocols and fostering a culture of cybersecurity security awareness are essential for long-term sustainability and business success in a digital world.
Recommendations for enhancing cyber preparedness and resilience
Conduct thorough risk assessments
Identifying potential cyber threats and vulnerabilities within the organization is the first step toward building a robust cybersecurity strategy. Regular risk assessments help businesses understand their risk landscape and prioritize their cybersecurity efforts.
Implement comprehensive incident response plans
Developing comprehensive incident response plans that include automated workflows and clear communication protocols is essential for effective incident management. These plans should be regularly tested and updated to ensure they remain relevant and effective.
Regular testing and updates
Regularly testing and updating incident response plans through simulations and drills ensures that organizations are prepared for real-world incidents. These exercises help identify gaps in the plans and provide opportunities for continuous improvement.
Continuous monitoring
Utilizing advanced tools and threat intelligence for continuous monitoring of the cyber threat landscape is crucial for staying ahead of potential threats. Continuous monitoring allows businesses to detect and respond to threats in real-time, reducing the risk of successful attacks.
Foster a culture of cybersecurity awareness
Involving all stakeholders in fostering a culture of cybersecurity awareness and preparedness across the organization is key to building resilience. Regular cybersecurity training and awareness programs help employees understand the importance of cybersecurity and their role in protecting the organization.
Key features of Everbridge for cyber preparedness
How do we support companies in delivering on those recommendations? Through the deployment of Everbridge 360. In particular, the Everbridge platform offers five key features to increase cybersecurity resilience and preparedness.

1. Real-time risk monitoring
Everbridge offers real-time risk monitoring to help organizations stay ahead of potential threats. This feature allows businesses to continuously assess their cybersecurity planning and identify vulnerabilities before they can be exploited.
2. Automated incident response workflows
Automated incident response workflows streamline the process of managing cyber incidents. By automating routine tasks, Everbridge reduces the time and effort required to respond to threats, enabling organizations to focus on more strategic activities.
3. Comprehensive communication tools
Effective communication is crucial during a cyber incident. Everbridge platform includes comprehensive communication tools that facilitate collaboration among different teams, ensuring that everyone is on the same page and that incident response efforts are coordinated.
4. Detailed reporting capabilities
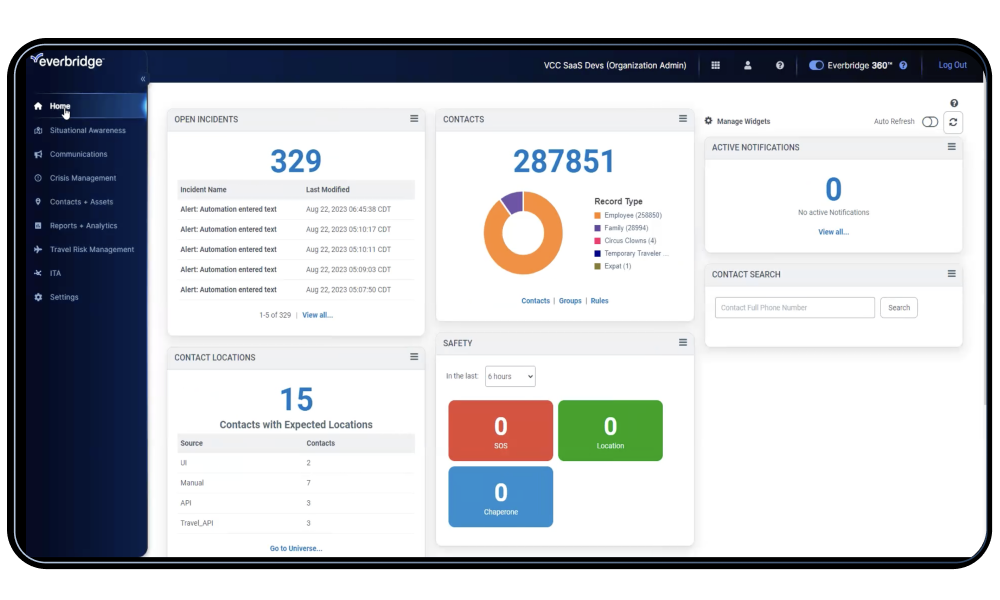
Detailed reporting capabilities provide organizations with insights into their cybersecurity performance. By analyzing data from past incidents, businesses can identify areas for improvement and refine their cybersecurity strategies.
Seamless integration with existing cybersecurity tools
One of the standout features of Everbridge is its ability to seamlessly integrate with existing cybersecurity tools and frameworks. This includes network security, Security Information and Event Management — SIEM — systems, threat intelligence platforms, and other security infrastructures. By leveraging current investments in cybersecurity, Everbridge enhances cyber resilience and ensures a unified approach to threat detection and response.
A step toward cybersecurity preparedness
In an era where cyber threats are becoming increasingly sophisticated and frequent, cybersecurity preparedness is more important than ever. By investing in proactive planning, risk assessment, and continuous monitoring, organizations can build resilience against cyber incidents and ensure operational continuity. Everbridge comprehensive platform offers the tools and capabilities needed to enhance cyber preparedness and manage cyber incidents effectively.
Take the first step toward building a resilient future with Everbridge.
Sign up for our exclusive webinar that will provide insights into the latest trends in cybersecurity and practical tips for building resilience. Attendees will learn from industry experts and gain valuable knowledge that can be applied to their own organizations.
By Lorenzo Marchetti, Everbridge Head of Global Public Affairs
In today’s digital landscape, enterprises heavily rely on their IT infrastructure for operational & business continuity. However, IT outages are inevitable and can disrupt business operations, leading to significant financial losses and reputational damage. Through its Everbridge 360 solution, Everbridge offers a comprehensive tool to support enterprises during these critical times, ensuring quick recovery and enhanced resilience.
Accelerated incident response and resolution for IT disruption
One of the most critical aspects of managing IT outages is the speed of response. Everbridge 360 with its digital operations solution streamlines workflows, providing contextual notifications and integrating with ChatOps to accelerate the assessment and response to IT disruptions. By pinpointing system degradations and supplying actionable issue context, Everbridge enables on-call resolvers to act swiftly and efficiently.
Key features to support in case of IT problems or IT emergency:
- Real-time risk monitoring: Continuous monitoring allows organizations to identify potential issues before they escalate into major IT outages.
- Automated incident response: Automated workflows and notifications ensure that the right personnel are alerted immediately, reducing the time to resolution.
Seamless integration with existing tools for system recovery
Everbridge integrates seamlessly with a variety of existing cybersecurity tools and frameworks. This compatibility ensures that organizations can leverage their current investments in technology while enhancing their incident response capabilities. The platform’s flexibility in integrating with Security Information and Event Management (SIEM) systems and other security infrastructure provides a unified approach to threat detection and response.
Benefits of IT outage management solutions:
- Unified threat management: Integration with existing tools ensures comprehensive threat management and streamlined operations.
- Automated workflows: Low- to no-code visual workflow designer allows teams to build and adapt automated runbooks and communication plans with ease.
Effective communication and coordination during an IT outage
During an IT outage, clear and effective communication is paramount. Everbridge’s platform facilitates this through multiple channels, including mobile apps, phones, SMS, and email. The platform’s automated escalations ensure that if the required personnel do not respond within a specified time, the issue is addressed by the right people without delay.
Communication tools for IT outage times:
- Context-rich notifications: Alerts are enriched with relevant context to ensure that responders have all the information they need to act quickly.
- Automated escalations: Ensures that critical issues are addressed by escalating alerts to the next level of response if initial contacts are unavailable.
Comprehensive post-incident analysis
After resolving an IT outage, it is essential to conduct a thorough analysis to understand the root causes and improve future response strategies. Everbridge offers comprehensive analytics and postmortem capabilities, providing real-time incident tracking, team performance visibility, and incident response efficacy. This continuous improvement process helps organizations adapt their incident response models and grow their resilience over time.
Post-incident capabilities:
- 360-degree postmortems: Detailed post-incident analysis helps in identifying gaps and improving response strategies.
- Continuous improvement: Real-time tracking and performance metrics aid in refining processes and preventing future outages.
Case study: Enhancing cyber resilience
A leading private research university faced challenges in coordinating responses to cyber-attacks and system outages due to the lack of a central tool. By leveraging Everbridge’s IT incident response platform, the university was able to enhance its cyber preparedness significantly. Automated workflows and real-time alerts enabled the university’s System Support team to restore normal operations faster than expected, minimizing financial and reputational damage.
Positive impact on recovery capabilities:
- Faster recovery: Automated workflows and real-time alerts reduced response time.
- Improved coordination: Centralized communication and coordination tools ensured all team members were on the same page.
IT outage management with Everbridge 360TM
Everbridge 360 and its digital operations solution provides enterprises with the tools they need to manage IT outages effectively. By accelerating incident response, integrating seamlessly with existing tools, ensuring effective communication, and offering comprehensive post-incident analysis, Everbridge helps organizations minimize IT disruption, reduce financial losses, and enhance their overall resilience. In an era where IT infrastructure is the backbone of business operations, Everbridge stands out as a critical partner in ensuring operational continuity and cyber resilience.
Leverage Everbridge solutions to operationalize your response to some of the points described in upcoming EU regulations including NISZ, DORA, and the Cyber Resilience Act. Enhance your compliance and strengthen your cyber defenses
In an increasingly interconnected world, the importance of robust cybersecurity measures cannot be overstated. The European Union (EU) has introduced several regulations aimed at enhancing cybersecurity across member states. These EU directives and regulations include the Directive on Measures for a High Common Level of Cybersecurity Across the Union (NIS2), the Digital Operational Resilience Act (DORA), and the Cyber Resilience Act (CRA).
This blog will explore how Everbridge solutions can help cyber security, risk, and compliance teams navigate these regulations to enhance their organization’s cybersecurity posture from an operational perspective.
Overview: NIS2, CRA and DORA
NIS2
The NIS2 Directive (Directive (EU) 2022/2555) aims to achieve a high common level of cybersecurity across the EU. The regulation took effect on 16 January 2023, and Member States have until 17 October 2024 to codify its measures into national law. It requires Member States to adopt national cybersecurity strategies and designate competent authorities, cyber crisis management authorities, and computer security incident response teams. It also imposes stricter security requirements, including security incident reporting and cooperation between member states. Consequently, companies operating in these sectors will have to strengthen their data protection measures and their incident response capabilities, under penalty of severe financial sanction.
DORA
The Digital Operational Resilience Act (Regulation (EU) 2022/2554) solves an important problem in the EU financial regulation. Before DORA, financial institutions managed the main categories of operational risk mainly with the allocation of capital, but they did not manage all components of operational resilience. With DORA, financial organizations are now mandated to ensure the resilience, continuity, and availability of their information and communication technology (ICT) systems while upholding stringent data security standards.
CRA
The Cyber Resilience Act (CRA) aims to safeguard consumers and businesses buying or using products or software with a digital component. It introduces mandatory cybersecurity requirements for manufacturers and retailers of such products. This regulation covers products that include digital elements enabling the transmission of data to a device or network. It also aims to promote trust in digital technologies by ensuring that they meet rigorous security standards. Manufacturers will therefore have to ensure that connected objects placed in the market comply with strict obligations such as a 24-hour notification window for any detected vulnerabilities.
Main challenges to concrete applications
NIS 2, CRA, and DORA regulations require significant effort in mapping dependencies, documentation, and planning. However, they do not explicitly address how to operationalize their plans to be able to withstand, respond to, and recover from business-impacting events. This represents a real challenge to companies, given the enhanced complexity and interdependency that these regulations cover.
Common organizational challenge in digital operations and cyber security
Many organizations have very siloed teams and tech stacks, which means collaboration during a business-impacting event can be very difficult; companies need tech that provides “information bridges” between the different business units. Without a technology solution that allows automated connection between monitoring, activation, collaboration, orchestration, and response, organizations will struggle.

How Everbridge supports companies to operationalize their compliance: automate and digitalize preparedness, communications & response, and reporting.
Everbridge provides a single hub for incident preparedness, risk monitoring, crisis management, and service reliability. In other words, through the Everbridge platform, companies will be able to adequately operationalize three key aspects: Preparedness, communication & response, and reporting. The Everbridge solutions are designed to proactively identify, assess, and monitor risk, respond instantly and accurately to every incident, safeguard digital and physical assets, and keep people safe and productive.
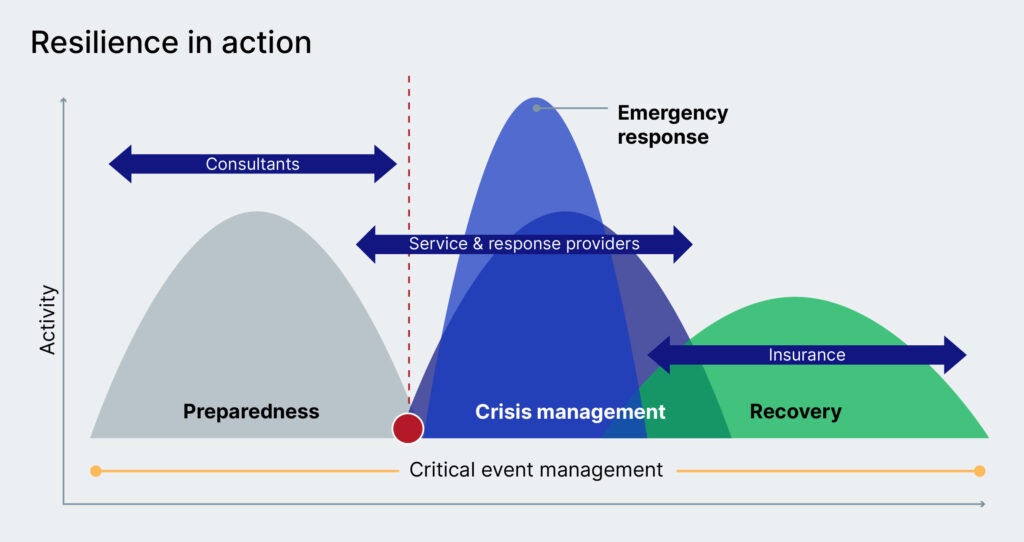
CEM resilience in action for emergency response
Preparedness – The Everbridge platform allows for the integration of all applicable systems to enable clear visibility across software applications and physical locations, giving a clear outline of what is important and why, and enabling faster decision-making and automation. Crucially, this step helps to identify key stakeholders and assets, which is one of the most important elements in responding to an event. Having data sets readily available and usable can improve response time and trigger workflows automatically rather than through manual intervention.
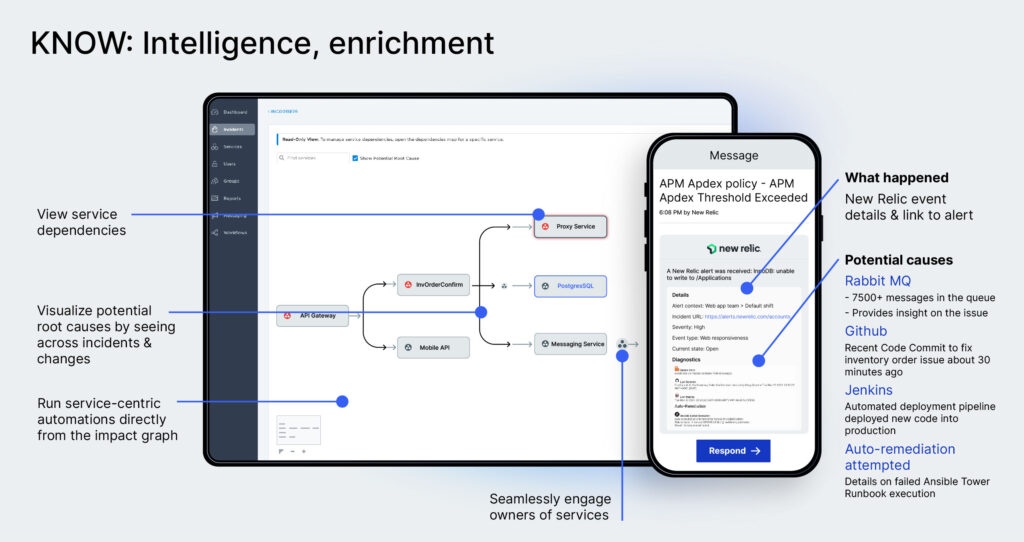
AI-powered information management with xMatters
Communications & response – Following the identification of the event and its impact, the Everbridge platform supports the orchestration of the response. This involves identifying any automation processes that can be initiated, aligning the response with the relevant Standard Operating Procedures (SOP) and ensuring tasks are assigned to the right people at the right time through “out of band” communications that are not dependent on infrastructure. By automating this process, Everbridge can slash response time down to minutes or seconds. Additionally, the Everbridge platform can be used to communicate with regulators as necessary, keeping relevant stakeholders updated, and visualize the status while providing estimates based on previous experience, which is particularly critical if the issue affects email.
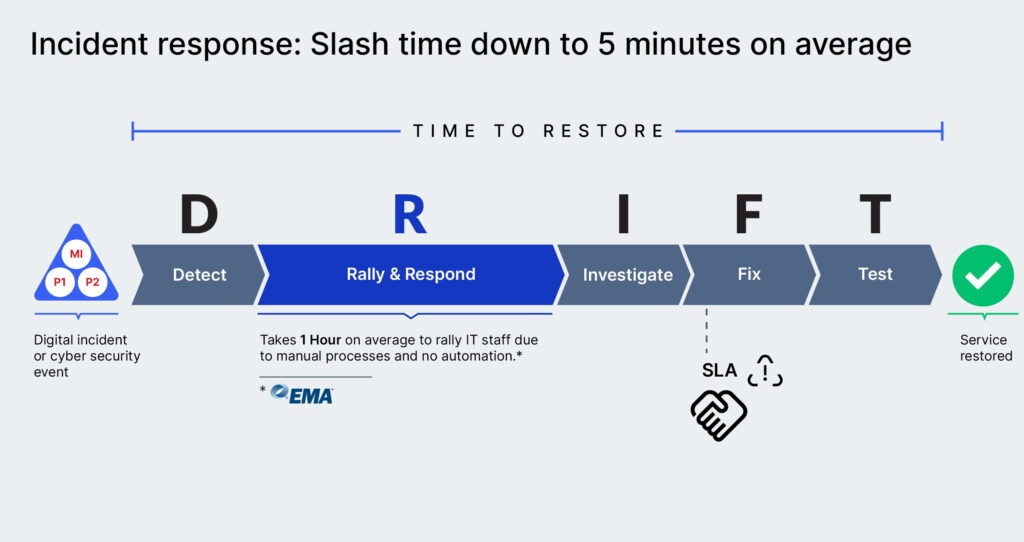
Incident response – time to restore
Reporting – The Everbridge platform allows organizations to develop self-assessment and learning capabilities for future preparation and response. During the event, all communications are captured, including but not limited to who received a communication, who responded, what the response was, and time of response. Also captured is whether there was no response at all. The same is also applicable for task allocation and completion for real-time monitoring during the event. Full audit logs are also recorded and exported for review/inclusion post-event. Within the simulation, situation reports can be generated when required and “After Action Reports” can be made available for review. All information is captured within the system to be utilized as required in After Action Reviews.
Dedicated solutions such as the Everbridge suite of products can play a critical role in helping organizations operationalize EU directives and regulations such as NIS2, DORA, and the CRA. By leveraging the Everbridge platform, cybersecurity and incident management teams enhance their cybersecurity posture and reinforce their compliance to these regulations through operational resilience. Everbridge enables teams to digitize response plans and connect them to monitoring and communications solutions. The platform enables automation, streamlines processes, enhances visibility, and empowers organizations to concretely demonstrate compliance by strengthening digital resilience.
Tracy Reinhold, Chief Security Officer, Everbridge discusses EU regulations and the power of the Everbridge platform to manage them with ISJ.
The Best in Resilience Certification affirms your organization’s readiness to manage any critical event that impacts organizations, assets, and resources.
In an interconnected world, digital resilience is crucial for navigating crises and safeguarding financial and security assets. The European Union (EU), comprising 27 countries and 450 million people, recognizes the significance of digital resilience and has introduced regulatory mandates to fortify and align the digital ecosystem. The latest addition to this landscape is the Digital Operational Resilience Act (DORA), alongside NIS2 and the Critical Entities Resilience Directive (CER), all effective since January 2023. This article explores the role of technology in responding to the DORA regulation and the opportunities it presents for organizations.
What is DORA?
The Digital Operational Resilience Act (Regulation (EU) 2022/2554) solves an important problem in the EU financial regulation. Before DORA, financial institutions managed the main categories of operational risk mainly with the allocation of capital, but they did not manage all components of operational resilience. With DORA, there is a significant change for the financial sector because organizations are now mandated to ensure the resilience, continuity, and availability of their information and communication technology (ICT) systems while upholding stringent data security standards. Aligned with existing regulations like NIS2 in the EU and the Bank of England Operational Resilience Regulation in the United Kingdom, DORA offers organizations the chance to leverage existing capabilities to meet the new requirements effectively. This regulatory framework lays the foundation for an efficient and agile risk management framework, compelling organizations to enhance their ICT risk management policies and procedures.
Compliance with DORA requires increased documentation to demonstrate adherence. Organizations must document their ICT and information assets, develop comprehensive encryption and cryptographic control policies, and establish protocols for network security management and data transfer protection. The Regulatory Technical Standards (RTS) further clarify DORA requirements. Organizations must conduct gap analyses to identify documentation gaps and validate processes and controls. Establishing governance processes to support these policies and ensuring long-term maintenance are crucial steps in achieving compliance.
The different components to Operationalize DORA: the role of Everbridge critical event management (CEM)
Although DORA offers a simplified ICT risk management framework for some organizations, governance, risk mitigation, ICT business continuity management, and reporting remain essential even within this simplified model. Implementing and maintaining this framework presents challenges, particularly for organizations with less formalized processes. It is crucial for organizations to assess their business strategies and identify applicable requirements for compliance.
Technology plays a pivotal role in enabling organizations to respond effectively to DORA compliance. Advanced software solutions, such as those offered by Everbridge, provide comprehensive support in meeting physical security, ICT security, and change management demands. They enable automation, streamline processes, and enhance visibility, empowering organizations to demonstrate compliance and strengthen digital resilience.
Operationalize DORA: Physical security
Physical security is crucial for overall digital resilience. Organizations must safeguard physical assets such as secure premises, data centers, and hardware equipment. Technology solutions can strengthen physical security measures by providing robust access control systems, surveillance systems, and incident management capabilities. These solutions enable organizations to monitor and manage physical access, detect and respond to security breaches in real-time, and ensure compliance with physical security policies.
Everbridge Smart Security allows organizations to centralize their physical security through Physical Security Information Management (PSIM) technologies, avoiding the costs of replacing physical devices. It facilitates the automation of standard operating procedures and response plans, as well as communicating with key stakeholders.
Operationalize DORA: Respond to business and people impacting events
Furthermore, as hybrid working trends continue, ensuring consistent protection for employees working from various locations becomes critical. Everbridge CEM for Business Operations and People Resilience provide organizations with the data repository and risk intelligence needed to identify potential risks and to communicate before, during, and after a crisis. These solutions will automate communications to impacted individuals, responders, and stakeholders, integrating with operationalized response plans.
Operationalize DORA: Digitizing operational resilience
ICT operations security includes capacity and performance management, data and systems security, vulnerability and patch management, and encryption and cryptographic controls. Technology solutions, like Everbridge CEM for Digital, address ICT operations security challenges. These solutions integrate with security monitoring and management systems, enabling organizations to identify vulnerabilities, monitor performance, and implement robust security controls. Automation and real-time alerts allow proactive detection and response to security incidents.
ICT change management involves managing changes to ICT systems, including project management, system development, acquisition and maintenance, and ICT change management requirements. Organizations must establish robust change management processes to minimize risks and ensure seamless operations.
Everbridge CEM for Digital offers an integrated approach to ICT risk management, facilitating collaboration, communication, and coordination among different teams. This technology solution integrates risk assessment, auto-remediation, incident management, and reporting capabilities, streamlining risk management processes and reducing the impact of events on the organization.
Complying with DORA presents many challenges. Technology solutions, like Everbridge CEM for Digital, streamline processes, automate tasks, and optimize resource utilization, offering cost-effective options for managing ICT risk and compliance requirements.
The way forward
Fostering a culture of resilience and risk management across the organization can be challenging. Technology solutions play a vital role in fostering this culture by providing intuitive interfaces, user-friendly workflows, and collaborative features. These solutions facilitate employee adoption and engagement, as well as centralized risk management processes.
While compliance with DORA may pose challenges, organizations can leverage the regulatory requirements as opportunities to drive innovation and gain a competitive edge. Advanced analytics, artificial intelligence, and machine learning capabilities allow organizations to gain actionable insights, proactively mitigate risks, and demonstrate commitment to digital resilience.
Everbridge empowers organizations to simplify compliance efforts and build operational resilience. Organizations can respond to business and people impacting events with Everbridge software solutions and drive better outcomes. Everbridge CEM operationalizes preparedness, automated communications, and reporting. By leveraging technology, organizations can embrace EU mandates on digital resilience, strengthen their ability to prevent crises, and better navigate the complexities of regulations effectively.
To learn more, watch the insightful webinar hosted by Everbridge, as we delve into the challenges and strategies faced by financial institutions in implementing strategies and tactics to comply with the European Union (EU) Directive on Operational Resilience Act (DORA).
Watch the on-demand webinar, Unlocking DORA, from Policy to Operationalization, or request a demo to understand how Everbridge can support organizations.